If you own something digital for communication and data processing, you can claim to have an Information System (IS)/digital footprint/tech stack. If you are involved in (legitimate) commerce, it would comprise of a computer, software platforms, and a phone at minimum. As your enterprise grows and evolves, so too must your IS. A strategic plan will guide your growth and cost-benefit analyses will allow for informed purchasing decisions.
With significant growth and potential industry clout on the horizon, the time will come to implement your foundational, base-level tech stack. There are loosely four pathways you can follow; your strategic plan and a cost-benefit analysis will determine which is best for you.
Purchase a pre-written application: this is a large and growing marketplace, with giants who deliver generic platforms to service many companies, business models, and business types. SAP and Salesforce are examples of two such heavyweights who can deliver these platforms. There are also niche products that focus on one industry or an industry segment and are specialised to cater for the needs of those businesses. A significant concern of following this pathway is that current and future needs must be met, or the system will quickly become obsolete.
Lease an application: products that can be bought and used as the backbone of an IS, can often, also be leased. Technical support and digital operations can then be handled, to varying degrees, by the creators of the platform. The system can be housed internally by lessee, or externally in the environment of the lessor.
Buy a license for open-source software: this arrangement allows the user to more closely tailor the IS to their needs as the software can be modified. The user can do this internally, but these services are also available from the provider.
Custom development: an organisation can outsource the development of their system or do it in-house. This process is costly and time consuming—the nature of IT projects can also make it riskier than the other three methods.
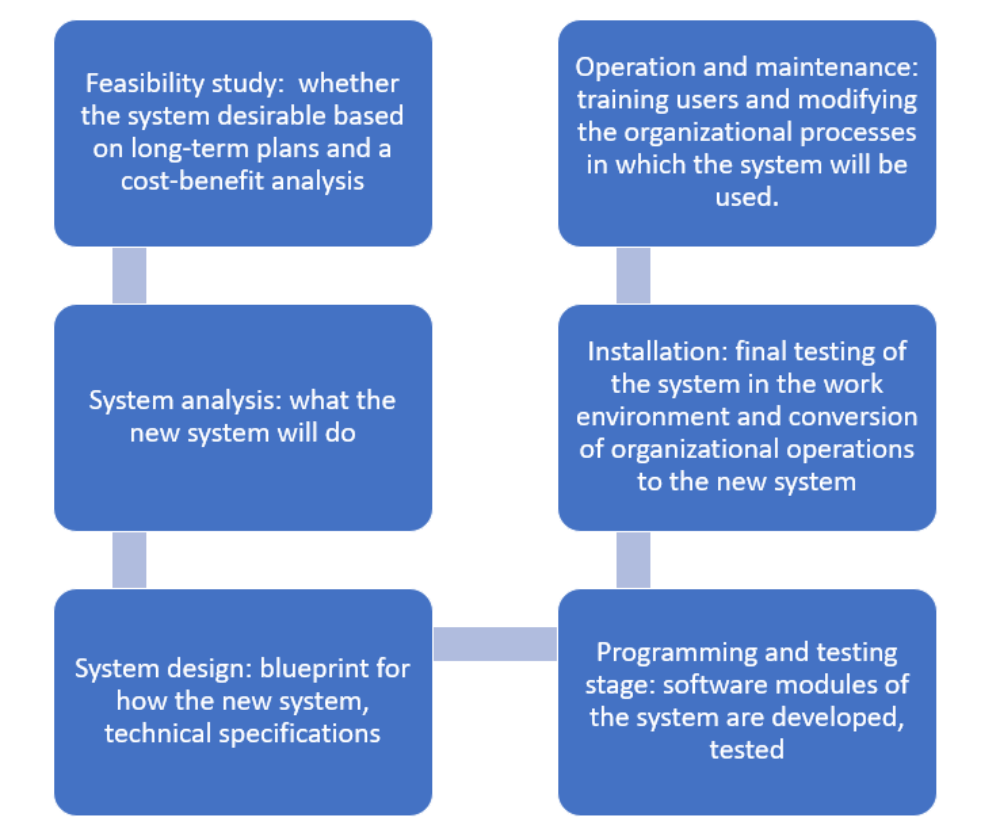
The sequence of events for developing enterprise information systems is mapped out in the diagram below.
This process is more aligned with the software development life cycle than the overarching project life cycle. The quality assured tech stack that is delivered is a pre-requisite for the ensuing, cyclical delivery of applications for internal or external audiences. Functionality and time are both critical. To ensure you meet the markets fluctuating needs, rapid application development (RAD) is a framework for achieving this.
Security considerations arise when enterprise operations require access to this class of information, and with that comes a range of controls. Best practice is to provide defence in depth with physical security at one end of the scale, data encryption at the other, and respect for all required measures in between. Risk analysis and assessment form part of the picture and will help the organisation navigate the inevitable oncoming roadblocks and barriers. IS, security, and risk audits will be ongoing for the life of the enterprise to ensure its health is maintained.
Digital interactions, services, and particularly commerce, rely on the disclosure of information. Nefarious activity exchanges information also, but players go to great lengths to muddy the waters and remove any connection to their real identity. Mission statements, core values, and policy indicate where an organisation is positioned ethically. Currently, all information has value, to varying extents, and its security falls to the company.
Privacy laws govern which behaviours are legal—responsibility for abiding by them and upholding stated values are the domain of the enterprise, its leadership, and all working within. Identification and protection against threat agents is required to meet these obligations. Internal or external, malicious or accidental, all threats are actions. Strategy and planning to protect against threats require governance and ongoing support from all stakeholders inside the organisation. Employee morale and a clear plan in response to the realisation of a threat action can significantly lower its impact.
The digital footprint of an organisation is likely to have some relationship with E-commerce, the cloud, intelligent systems and AI, and social computing. The nature of interactions and connections should be responsive to the ongoing changes in the digital landscape.